And why does it affect Ajit Pai - a member of the FCC - enough to write an op-ed in the Washington Post?
http://www.washingtonpost.com/opinions/truthy-project-is-unworthy-of-tax-dollars/2014/10/17/a3274faa-531b-11e4-809b-8cc0a295c773_story.html
Head of the article saved here for posterity...
Ajit Pai is a member of the Federal Communications Commission.
If
you take to Twitter to express your views on a hot-button issue, does
the government have an interest in deciding whether you are spreading
“misinformation’’? If you tweet your support for a candidate in the
November elections, should taxpayer money be used to monitor your speech
and evaluate your “partisanship’’?
My guess is that most
Americans would answer those questions with a resounding no. But the
federal government seems to disagree. The
National Science Foundation
, a federal agency whose mission is to “promote the progress of
science; to advance the national health, prosperity and welfare; and to
secure the national defense,” is funding a project to collect and
analyze your Twitter data.
The project is being developed by
researchers at Indiana University, and its purported aim is to detect
what they deem “social pollution” and to study what they call “social
epidemics,” including how memes — ideas that spread throughout pop
culture — propagate. What types of social pollution are they targeting?
“Political smears,” so-called “astroturfing” and other forms of
“misinformation.”
Named “Truthy,” after a term coined by TV host
Stephen Colbert,
the project claims to use a “sophisticated combination of text and data
mining, social network analysis, and complex network models” to
distinguish between memes that arise in an “organic manner” and those
that are manipulated into being.
But there’s much
more to the story. Focusing in particular on political speech, Truthy
keeps track of which Twitter accounts are using hashtags such as
#teaparty and #dems. It estimates users’ “partisanship.” It invites feedback on whether specific Twitter users,
such as the Drudge Report,
are “truthy” or “spamming.” And it evaluates whether accounts are
expressing “positive” or “negative” sentiments toward other users or
memes.
The Truthy team says this research could be used to “
mitigate the diffusion of false and misleading ideas, detect hate speech and subversive propaganda, and assist in the preservation of open debate.”
I'm so happy they have my best interests at heart
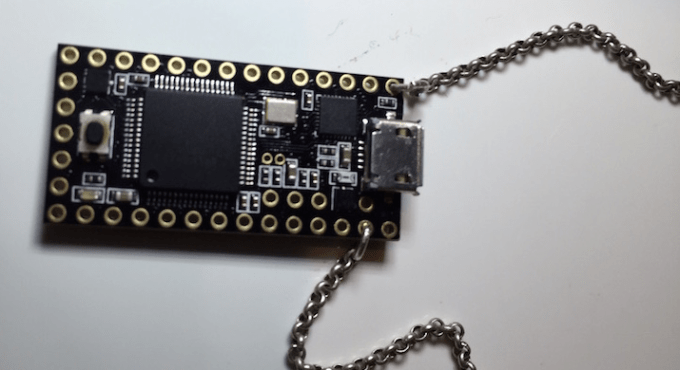 Tech Crunch brings us a cool USB hacking tool here
Tech Crunch brings us a cool USB hacking tool here